Exactly How BQT Locks Supply Reliable Protection for Your Home
Exactly How BQT Locks Supply Reliable Protection for Your Home
Blog Article
The Future of Safety And Security: Checking Out the most recent Fads in Electronic Safety And Security Technologies
Digital safety and security technologies have actually ended up being progressively advanced, offering innovative remedies to address the ever-growing difficulties dealt with by individuals and organizations alike. From biometric verification to the integration of artificial intelligence and equipment knowing, these fads hold the assurance of improving safety and security steps in extraordinary ways.
Surge of Biometric Authentication
With the increasing demand for protected and convenient verification techniques, the surge of biometric authentication has revolutionized the method individuals gain access to and shield their sensitive details. Biometric authentication makes use of one-of-a-kind biological characteristics such as fingerprints, facial features, iris patterns, voice acknowledgment, and also behavior traits for identity confirmation. This innovation supplies a much more reputable and secure approach contrasted to conventional passwords or PINs, as biometric information is extremely challenging to reproduce or swipe.
Among the vital advantages of biometric verification is its comfort. Users no more need to bear in mind complex passwords or stress about shedding access as a result of failed to remember qualifications. By just making use of a part of their body for confirmation, individuals can quickly and securely gain access to their devices, accounts, or physical areas.
Moreover, biometric authentication boosts protection by offering an extra robust protection against unapproved accessibility. With biometric markers being one-of-a-kind to each person, the risk of identification burglary or unauthorized access is considerably lowered. This increased degree of safety is specifically vital in sectors such as financing, medical care, and government where securing delicate information is vital.
Integration of AI and Artificial Intelligence
The development of digital safety and security technologies, exemplified by the rise of biometric verification, has led the means for developments in the assimilation of AI and Machine Knowing for enhanced identification and security devices. By leveraging AI algorithms and Artificial intelligence models, electronic protection systems can now examine huge amounts of data to detect patterns, anomalies, and potential risks in real-time. These innovations can adjust to evolving safety and security risks and supply aggressive feedbacks to mitigate risks successfully.
One substantial application of AI and Equipment Understanding in digital protection remains in anticipating analytics, where historic information is made use of to anticipate prospective safety and security breaches or cyber-attacks. This proactive approach allows security systems to anticipate and protect against hazards prior to they happen, enhancing total safety and security measures. In addition, AI-powered monitoring systems can wisely monitor and analyze video clip feeds to determine questionable activities or people, enhancing action times and decreasing duds.
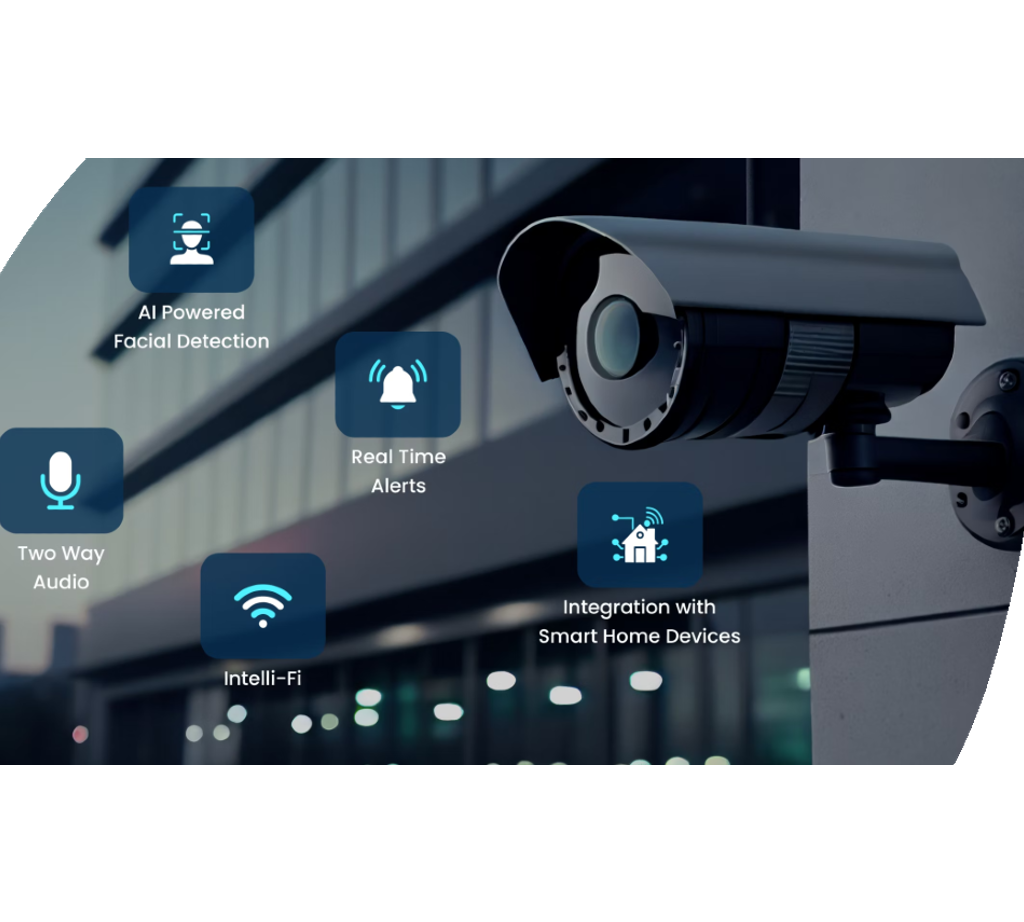
IoT and Smart Safety Tools
Developments in electronic protection modern technologies have actually resulted in the emergence of IoT and Smart Protection Gadgets, revolutionizing the means safety systems operate. The Net of Things (IoT) has made it possible for safety and security gadgets to be interconnected and from another location obtainable, providing improved monitoring and control capabilities. Smart Protection Devices, such as clever cameras, door locks, and movement sensors, are outfitted with functionalities like real-time signals, two-way communication, and assimilation with other smart home systems.
Among the substantial benefits of IoT and Smart Safety And Security Tools is the ability to offer customers with seamless access to their protection systems through mobile phones or various other internet-connected tools. This ease permits remote tracking, equipping, and deactivating of protection systems from anywhere, offering homeowners with peace of mind and versatility. These gadgets frequently integrate sophisticated attributes like facial recognition, geofencing, and activity pattern recognition to enhance overall safety and security levels.
As IoT continues to see this develop, the combination of expert system and maker discovering algorithms into Smart Safety and security Gadgets is expected to further improve discovery precision and modification choices, making electronic safety and security systems even more reliable and trusted.
Cloud-Based Protection Solutions
Arising as an essential element of modern digital safety facilities, Cloud-Based Safety and security Solutions offer unrivaled adaptability and scalability in guarding digital assets. By leveraging the power of cloud computer, these options offer businesses with innovative safety features without the demand for substantial on-premises hardware or framework. Cloud-based safety and security services make it possible for remote tracking, real-time alerts, and systematized administration of security systems from any type of place with an internet connection. This not only improves benefit yet likewise enables fast responses to protection events.
In addition, cloud-based security services provide automatic software updates and maintenance, ensuring that safety and security systems are always current with the most current defenses versus emerging risks. In general, cloud-based security services stand for a cost-efficient and reliable method for services to improve their security stance and shield their electronic possessions.
Focus on Cybersecurity Procedures
With the enhancing sophistication of cyber hazards, services are putting a paramount concentrate on boosting their cybersecurity procedures. BQT Solutions. As technology breakthroughs, so do use this link the methods used by cybercriminals to breach systems and take sensitive info. This has actually motivated organizations to invest greatly in cybersecurity procedures to shield their information, networks, and systems from harmful attacks
Among the key patterns in cybersecurity is the adoption of innovative encryption protocols to guard data both at rest and en route. Encryption assists to make certain that even if data is obstructed, it continues to be unreadable and protected. In addition, the execution of multi-factor authentication has visit here come to be increasingly common to add an additional layer of security and confirm the identifications of customers accessing delicate information.
Final Thought

Report this page